Cyber Insecurity
The headline read: “Nation State-sponsored Attackers Hacked Two Airports, Report Says.”
This headline appeared in June after a cooperative effort between the federal government and the Center for Internet Security (CIS) thwarted a prolonged operation to spy on aviation systems at 75 U.S. airports, but not before hackers breached the networks of two of them.
Authorities actually discovered this threat in 2013, when the federal government notified CIS about an advanced persistent threat (APT) targeting airports.
Typically APTs involve Nation State attackers employing sophisticated methods to creep around a network for as long as necessary to obtain the information they seek. In this case the attackers sent spear phishing emails to aviation personnel that contained vulnerabilities that the CIS reports were difficult to detect and execute.
This is not a rare event; in fact it’s one that is happening far more frequently than ever before. According to the annual CIS report, there were 48 significant computer security incidents in 2013, more than double the number recorded in 2012.
It’s also something that’s happening globally. In late September, news media reported hackers broke into the server of India’s largest airport operator, the Airports Authority of India, and stole crucial data including financial information, payroll, and more.
“Here’s the scary part about these incidents: They are attacking and targeting airports--and nobody really knows why,” says Andre Allen, information and cyber security manager at GSC Inc., an international software and technology firm in the airport space.
Not only that but, according to Mark Gazit, CEO of Theta Ray, a national firm offering cyber security solutions, the average time to discover a threat is approximately 240 days. But, he adds, it can take a month or more for an organization to recover.
Even more concerning are the words of Dom Nessi, deputy director/chief information officer at Los Angeles World Airports (LAWA): “I think airports have a long ways to go, both in the United States and internationally, to meet the challenges of today’s cyber threat. That’s not to say that individual airports haven’t excelled in terms of cyber security, but many airports still have work to do.”
Causes of Cyber Insecurity
Dr. John McCarthy, cyber security fellow at Cranfield University and head of research with the International Centre for Airport Cyber Research, says airport systems are extremely vulnerable to attack for three key reasons:
- Airports are very political environments with many different stakeholders. Just getting all the stakeholders in the same room to discuss a common problem can be an issue, he says, adding that many times all those managing vulnerable systems aren’t even included in the discussions about cyber security.
- The Cloud. As airports migrate to the Cloud, it’s critical to know who owns the data and how it’s being managed. But those things are not always considered, he says.
- Airports are cost driven. Without adequate funding, airports might not invest in the technologies and people needed to secure their networks.
- All airport systems, from the baggage handling system to the moving walkways to the security cameras, reside on a single network, and can be remotely controlled—a boon for system operators but an inherent security risk. “There are multiple operations, from multiple vendors, all residing on the same network,” McCarthy, cyber security team leader for ServiceTec, says. “But these systems were never designed to put on public networks and it’s a huge problem.”
Couple those issues with the explosive expansion of broadband and you have a problem of epic proportions. “Now everyone is on the Internet. Everything is accessible from everywhere at all times,” he says. “But we haven’t embraced this in terms of our own security.”
Where Vulnerabilities Lie
According to Nessi, safety and security systems, baggage and handling technology, and the building’s facility control systems are attractive targets for cyber crooks. But in stark contrast, says McCarthy, most airport cyber security efforts focus on the traditional IT network, and not on these systems.
“Recent technological developments and moves to increase efficiency have resulted in the merging of traditional IT networks with SCADA (Supervisor Control and Data Acquisition Systems). Now airports often have homogenous networks that are bolted together with cyber security as an after thought,” explains McCarthy in “Cybersecurity: Keeping Cyber Secure.”
This phenomenon means that some of the more innocuous appearing systems pose the most risk. For instance, many people would not lump industrial control systems into their cyber vulnerabilities. But HVAC, airfield lighting, automated parking systems, automated people movers, and baggage systems all provide entry points into an airport’s network.
“These systems are at risk because most people don’t think that these systems are being targeted,” Allen says. “They don’t even think of them as being connected to the Internet. If you don’t at least start looking at your risk associated with your critical systems and putting some controls around them, you’re very vulnerable.”
Another area to consider, says McCarthy, is the airport Website. MCarthy recently performed a hacking demo at an airport in Rome where he breached their Website and placed a message on it. “A hacker could cause colossal damage to an airport through a system most people don’t even think to protect,” he says. “They hack into the Website, change your parking URL to a nearly identical one that they own, send out a phishing email to your customers telling them they’ll get 50 percent off their parking if they book online, and all of this money goes to the hackers. And they haven’t even touched the IT system in the airport!”
Digital Defenders
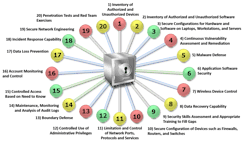
Nessi recommends taking the Defense in Depth approach to cyber security. Defense in Depth is defined as the coordinated use of multiple security countermeasures to protect the integrity of an organization’s information assets. The idea is that it’s more difficult to defeat a complex and multi-layered defense system than to penetrate a single barrier.
Defense in Depth minimizes the probability that malicious hackers will succeed by employing a well-designed strategy that aids system administrators and security personnel in identifying attempts to compromise a computer, server, proprietary network or ISP (Internet service provider). Should a hacker gain access, Defense in Depth minimizes adverse impacts and gives administrators time to deploy new or updated countermeasures to prevent recurrence.
This strategy utilizes antivirus software, firewalls, anti-spyware programs, hierarchical passwords, intrusion detection and biometric verification. “On your perimeter, you have firewalls and intrusion detection systems, and a variety of systems that monitor and protect your network,” Nessi says. “You have technology to protect your data and technology to protect your applications. You have technology that protects your interaction on the Web. You have technology that protects your desktop environment. And now we have technology that protects our mobile devices.”
Allen recommends also adding application-wide listing to the airport cyber security arsenal, noting that this technology can prevent up to 80 percent of the threats trying to sneak in. This technology locks down a computer so that it will only operate those applications a user needs to perform his or her job. If a user clicks on an email containing malware, the malware won’t execute and the technology quarantines it. “This gives network administrators time to respond and deploy their defenses,” he says.
Though technology used in the Defense in Depth strategy aids in early detection by looking for suspicious network activity, it may not be enough and threats may still slip through. Gazit stresses, “Early detection is one of the biggest holes in cyber security today. It’s unacceptable to think about an airport or an airplane that doesn’t have smoke detectors. But we don’t always have cyber attack detectors in airports. Yet detection is an extremely important part of cyber security.”
And while technology can cull through the network looking for suspicious activity, human eyes still need to review these logs every single day, warns Nessi. “Analysts need to look at these logs to see if there is anything there,” he says. “If they think there is something going on, they need to report it.”
The Human Factor
“People forget the Internet was built with very few safeguards internally. It was built for transmitting traffic in data packets. It was built to facilitate communication. The human element of it has made it a dangerous place to be,” Nessi says.
For this reason, Defense in Depth also includes training and education of employees. LAWA provides annual cyber security training for its workers. Allen says as head of the City of Houston’s cyber networks, he instituted mandatory security awareness training for all employees.
“Good cyber hygiene translates to good cyber security,” McCarthy says. “We need to educate all levels of the organization in sound simple practices. Airports could stop 90 percent of all cyber security issues by properly training all members of the organization.”
Nessi agrees: “Most problems start at home. You need to make sure your organization is educated and you have policies in place.”
The Multi-State Information Sharing and Analysis Center is considered by many as ‘the’ focal point for cyber threat prevention, protection, response and recovery for the nation's state, local, tribal and territorial governments. This CERT organization offers Web based training that Allen says can greatly enhance employees’ cyber security knowlege. Employees can take the training, which start to finish averages about three hours, as they have time.
Training should cover good cyber hygiene, which McCarthy describes as everything from password protection, to phishing emails, to forbidding the use of USB devices. He explains that most people see USB devices as secure but they are actually one of the most common ways to infect a network. “People plug those into a machine and format them, which erases evidence of a virus, but by then it’s already contaminated the system,” he says.
LAWA also monitors traffic to see what employees are doing on the network and blocks sites such as Facebook and Twitter because as Nessi says: “Not only are they distractions but there is the potential for malware on these sites.”
“The utilization of your organization’s system is not a personal right of an employee,” he explains. “Anything and everything done on a work computer is subject to review by the organization. Probably 50 percent of all organizations allow some personal browsing on the Internet as long as it doesn’t interfere with work. But in other organizations that’s prohibited. Every organization has a different threshold for risk.”
Acceptable use policies presented at orientation teach employees what their limits are, according to Allen. “You have to start with policies so that at least employees know what they can and cannot do,” he says. “They know that these are the things they will be accountable for.”
The caveat, however, is that “none of this will happen without any money,” he adds. “If you’re not going to fund it, then you’ll just wait until you get hacked. And airports will get hacked eventually. That’s one of the things the ACRP (Airport Cooperative Research Program) said upfront. They said there will be apathy until an attack occurs because there is a lack of direct economic incentives to do it.”
But as Target and Home Depot learned when their systems were breached, the economic impact can be in the hundreds of millions of dollars. “The moment they start understanding the connection between cyber security and their business, they’ll get serious about the funding,” he says.
A