Every day we’re at risk of having our own personal identity and financial information stolen. If that happened to an individual it would be a very difficult situation. But when it happens to businesses which are responsible for securing the personal information of customers, it becomes a major liability, one which can quickly put a company out of business entirely. According to the Identify Theft Resource Center, the number of data breaches rose nearly 50 percent in 2008. Nearly 40 percent of all reported breaches targeted businesses, at an average cost per record breached of $202. With fines, audit fees, and replacement costs, the typical Level 4 merchant can expect to pay upwards of $36,000 for a breach.
And, while hackers are a major concern, 35 percent of breaches occur as the result of human error, such as lost laptops, inadvertent posting of confidential data online, files tossed into the trash, etc.
However, a prudent business will take precautions. Becoming PCI-compliant will guide a company through those steps in an organized fashion, and may help to mitigate some of the penalties which would be imposed if a breach occurs.
While PCI compliance is not currently a federal law, several states have laws that are already in effect to enforce components of the PCI Data Security Standard, and more legislatures are working on similar legislation. (There are many good sources of information about PCI, including the helpful website at www.pcicomplianceguide.org.)
Defining PCI Compliance
The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure that all companies that process, store, or transmit credit card information maintain a secure environment.
The Payment Card Industry Security Standards Council is an independent body that was created by the major payment card brands (Visa, MasterCard, American Express, Discover, and JCB) to manage the development and ongoing evolution of security standards for the Payment Card Industry (PCI). The PCI Data Security Standard has been updated several times since its release in 2006. The PCI DSS and details of the compliance process are available on the council’s website at www.pcisecuritystandards.org. It is important to note that the payment brands and acquiring banks are responsible for enforcing compliance, not the PCI council.
Who must Comply?
PCI applies to all organizations or merchants, regardless of size or number of transactions, that accepts, transmits, or stores any cardholder data. Said another way, if any customer of a company ever pays the merchant directly using a credit card or debit card, then the PCI DSS requirements apply.
Deadlines
All merchants must be compliant now. To recap the schedule:
• Beginning October 1, 2008, Credit Card Processors and Bank Card Acquirers could only accept new merchants that are PCI/DSS-compliant or that utilize PA/DSS-compliant applications.
• Beginning October 1, 2009, all payment applications which are not PA/DSS-compliant were decertified.
• Beginning July 1, 2010, Credit Card Processors and Bank Card Acquirers must insure that merchants and agents use only PA/DSS-compliant applications.
Merchant Requirements for Compliance
There are 12 basic requirements which a merchant must meet in order to become certified as PCI-compliant, organized into six areas. Each of these requirements is noted below. However, a company must familiarize itself with the many details of each requirement as set forth in the PCI
Data Security Standard documentation.
• Build and Maintain a Secure Network
1) Install and maintain a firewall configuration to protect cardholder data.
2) Do not use vendor-supplied defaults for system passwords and other security parameters.
• Protect Cardholder Data
3) Protect stored cardholder data.
4) Encrypt transmission of cardholder data across open, public networks.
• Maintain a Vulnerability Management Program
5) Use and regularly update anti-virus software.
6) Develop and maintain secure systems and applications
• Implement Strong Access Control Measures
7) Restrict access to cardholder data by business need-to-know.
8) Assign a unique ID to each person with computer access.
9) Restrict physical access to cardholder data.
• Regularly Monitor and Test Networks
10) Track and monitor all access to network resources and cardholder data.
11) Regularly test security systems and processes.
• Maintain an Information Security Policy
12) Maintain a policy that addresses information security
Demonstrating Compliance
To demonstrate compliance, a small-to-medium sized business (Level 4 merchant) must complete the following steps:
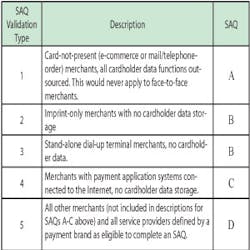
• Identify the company’s Validation Type as defined by PCI DSS (see graphic). This is used to determine which Self-Assessment Questionnaire is appropriate for the particular business.
• Complete the Self-Assessment Questionnaire according to the instructions in the Self-Assessment Questionnaire Instructions and Guidelines.
• Complete and obtain evidence of a passing vulnerability scan with a PCI/SSC-Approved Scanning Vendor (ASV). Note that scanning does not apply to all merchants. It is required for Validation Type 4 and 5 — those merchants with external-facing IP addresses. Basically, if a company electronically stores cardholder information or if its processing systems have any Internet connectivity, a quarterly scan by an approved scanning vendor is required.
• Complete the relevant Attestation of Compliance in its entirety (located in the SAQ tool).
• Submit the SAQ, evidence of a passing scan (if applicable), and the Attestation of Compliance, along with any other requested documentation, to the company’s acquirer.